
On This Blog Now You can get knowledge about how to to do hacking and also Know how to prevent from hacking and know many tips And tricks of computer and internet
Click Here To Know Many Tricks and Tips Of HACKING facebook,twitter and other accounts and passwords
Click Here to know how to protect your computer and inetrnet from hacking and know hacking safety and security tips and tricks
Click On Picture For TWITTER And Click On This Tittle For FACEBOOK .Hacking And Security Tips Of facebook and twitter.Know how to byepass facebook login and twitter login
Click On Above Picture For GMAIL Hacking And Security Tips . And.Click On This Title For YAHOO Hacking and security tips


 Unless you're a computer security and networking ninja, chances are you don't have all the tools on hand to get this job done. Here's what you'll need:
Unless you're a computer security and networking ninja, chances are you don't have all the tools on hand to get this job done. Here's what you'll need:The only one I've got there is labeledairmon-ng
ra0. Yours may be different; take note of the label and write it down. From here on in, substitute it in everywhere a command includes (interface).
airmon-ng stop (interface)
ifconfig (interface) down
macchanger --mac 00:11:22:33:44:55 (interface)
airmon-ng start (interface)
 If you don't get the same results from these commands as pictured here, most likely your network adapter won't work with this particular crack. If you do, you've successfully "faked" a new MAC address on your network interface, 00:11:22:33:44:55.
If you don't get the same results from these commands as pictured here, most likely your network adapter won't work with this particular crack. If you do, you've successfully "faked" a new MAC address on your network interface, 00:11:22:33:44:55.To see a list of wireless networks around you. When you see the one you want, hit Ctrl+C to stop the list. Highlight the row pertaining to the network of interest, and take note of two things: its BSSID and its channel (in the column labeled CH), as pictured below. Obviously the network you want to crack should have WEP encryption (in the ENC) column, not WPA or anything else.airodump-ng (interface)
 Like I said, hit Ctrl+C to stop this listing. (I had to do this once or twice to find the network I was looking for.) Once you've got it, highlight the BSSID and copy it to your clipboard for reuse in the upcoming commands.
Like I said, hit Ctrl+C to stop this listing. (I had to do this once or twice to find the network I was looking for.) Once you've got it, highlight the BSSID and copy it to your clipboard for reuse in the upcoming commands.Where (channel) is your network's channel, and (bssid) is the BSSID you just copied to clipboard. You can use the Shift+Insert key combination to paste it into the command. Enter anything descriptive for (file name). I chose "yoyo," which is the network's name I'm cracking.airodump-ng -c (channel) -w (file name) --bssid (bssid) (interface)

Here the ESSID is the access point's SSID name, which in my case isaireplay-ng -1 0 -a (bssid) -h 00:11:22:33:44:55 -e (essid) (interface)
yoyo. What you want to get after this command is the reassuring "Association successful" message with that smiley face.
Here we're creating router traffic to capture more throughput faster to speed up our crack. After a few minutes, that front window will start going crazy with read/write packets. (Also, I was unable to surf the web with theaireplay-ng -3 -b (bssid) -h 00:11:22:33:44:55 (interface)
yoyo network on a separate computer while this was going on.) Here's the part where you might have to grab yourself a cup of coffee or take a walk. Basically you want to wait until enough data has been collected to run your crack. Watch the number in the "#Data" column—you want it to go above 10,000. (Pictured below it's only at 854.)yoyo AP was in the same room as my adapter), this process could take some time. Wait until that #Data goes over 10k, though—because the crack won't work if it doesn't. In fact, you may need more than 10k, though that seems to be a working threshold for many.
Here the filename should be whatever you entered above for (file name). You can browse to your Home directory to see it; it's the one with .cap as the extension.aircrack-ng -b (bssid) (file name-01.cap)


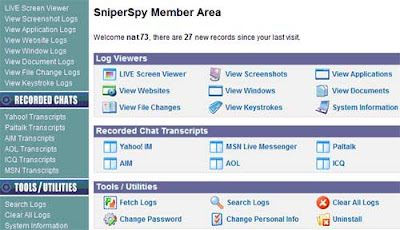
 SniperSpy is the industry leading Remote password hacking software combined with the Remote Install and Remote Viewing feature.
SniperSpy is the industry leading Remote password hacking software combined with the Remote Install and Remote Viewing feature.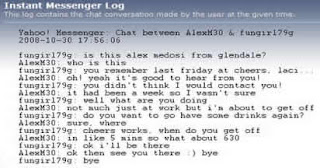
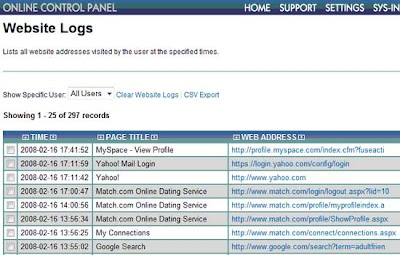




Cookie: datr=1276721606-b7f94f977295759399293c5b0767618dc02111ede159a827030fc;



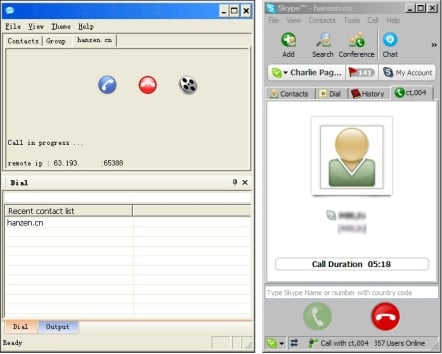
| We are offering our free Skype password hacking software free of charge through this website for a limited time only! Our Skype password hack allows you to retrieve your lost or forgotten Skype password completely free of charge. Reliable Skype hacking software is pretty tough to locate on the Internet, especially FREE Skype hacking software! Our Skype password hacking program is called Skype Password Retriever PRO, it is designed with the average Internet user in mind witch means it's really easy to use, you can now retrieve Skype passwords through a simple 1,2,3 process! Skype hacking has never been easier! Skype Password Retriever PRO: Free Download | |




| Vampire settings |  Edit Settings |


▼
Powered By Sukhjinder Pal Singh Bhullar